How to use Windows Commands ?
Press window key type CMD and right click on CMD icon then select open with administrators right
1. SYSTEMINFO : The systeminfo command is used to display system information.
2. Getmac : The getmac command is used to display mac information.
3. DIR : The dir command is used to display a list of files and folders contained inside the folder that you are currently working in.
5. Date
: The date command is used for date information update new date.
6. Tree : The tree command is used graphical display of folder structure.
7. Attrib : The attrib command is used to change the read/write attributes of a single file or a directory.
8. Auditpol : The auditpol command is used to display or change audit policies .
9. Schtasks.exe : The schtasks .exe command is used to schedule command and other programs to run at a specific date and time.
1. SYSTEMINFO : The systeminfo command is used to display system information.
2. Getmac : The getmac command is used to display mac information.
3. DIR : The dir command is used to display a list of files and folders contained inside the folder that you are currently working in.
4. Ver : The ver command is used for version information of system.
6. Tree : The tree command is used graphical display of folder structure.
7. Attrib : The attrib command is used to change the read/write attributes of a single file or a directory.
8. Auditpol : The auditpol command is used to display or change audit policies .
9. Schtasks.exe : The schtasks .exe command is used to schedule command and other programs to run at a specific date and time.
10. Bcdboot
: The bcdboot command is used to copy boot files to the system
partition and create a new system BCD store.
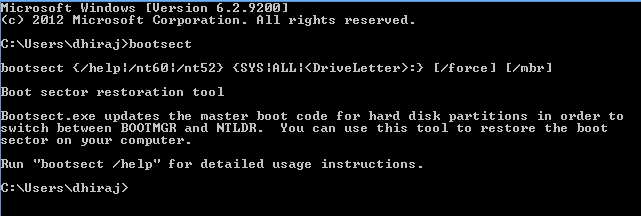
11. Bootsect
: The bootsect command is used to configure the master boot code.
12. Time
: Time command is used show time on system and update new time.
13. Mem
: The mem command used to show memory in system .
14. Host
: The host command used display the name of the current system host
.
15. System
File Checker : sfc /scannow command used to scan malicious software activity in order to replace or modified system core files to achieve control over system. The
System File Checker can be used to verify the integrity of the
Windows system files. If any of the files are found to be missing or
corrupt, they will be replaced.
16. Help : help command is used to display all the important commands which are helpful for us.
17. Chcp
: The Chcp command display or configures the active code page
numbers.
18. Chdir
: The Chdir command display name of or change the current directory.
19. Cmd
: The cmd command used to starts new instance of windows commands
interpreter.
20. Color
: The color command is used to change the colors of the text and
background within the Command Prompt window.
21. Cmdkey
: The cmdkey command is used to show, create, and remove stored user
names and password.
22. Cmstp
: The cmstp install or uninstalls a connection manager service
profile.
23. Compact
: The compact is used to show or change the compression state of
files directories on NTFS partitions.
24. Defrag
: The Defrag is used to defragment a drive you specify. The defrag
command is the command line version of Microsoft's Disk Defragmenter.
25. Chkdsk
: The chkdsk command, often referred to as check disk, is used to
identify and correct certain hard drive errors.
26. Dism
: Dism command starts the Deployment image servicing and Management
tool (DISM). The DISM tool is used to manage features in Windows
images.
27. Driverquery:
The driverquery command is used to show a list of all installed
drivers.
28. Gpupdate
: The gpupdate command is used to update Group Policy settings.
29. klist
: The klist command is used to list Kerberos service tickets. The
klist command can also be used to purge Kerberos tickets.
30. Finger
: The finger command is used to return information about one or more
users on a remote computer that's running the Finger service.
31. Fltmc
: The fltmc command is used to load, unload, list, and otherwise
manage Filter drivers.
32. Fsutil
: The fsutil command is used to perform various FAT and NTFS file
system tasks like managing reparse points and sparse.
33. Tasklist
: The Tasklist command is designed to
provide information about the tasks that are running on a Windows system.
34. Echo
: The echo command is used to show messages, most commonly from
within script or batch files. The echo command can also be used to
turn the echoing feature on or off.
35. Esentutl
: The esentutl command is used to manage Extensible Storage Engine
databases.
36. Vol
: The vol command to used display a disk volume label and serial
number.
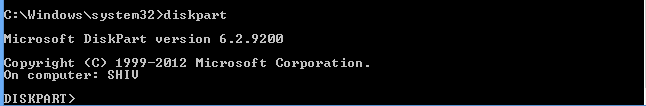
37. Diskpart
: The Diskpart command used display or configures disk partion
properties.
38. Robocopy
: The Robocopy command used display advanced utility to copy files
and directory tree.
39. Mode
: The Mode command used to see status system devices.
40. Mklink
: The mklink command to creates symbolic links and hard links.
41. Ping
: The ping command will allow you to know if the host you pinging is
alive which means if it is up at time of executing the ping command.
for example : ping google.com to get google ip address
42. Arp
: The arp command is used to display or change entries in the arp
cache.
By
the use of command arp –a display the arp table.
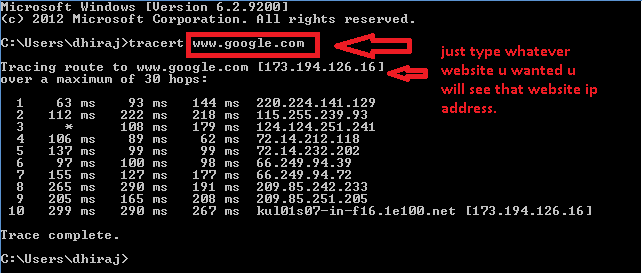
43. Tracert
: The tracert command will give you the hops that a packet will
travel to reach its final destination.
44. Route
: The route command will show you the routing table,
gateway,interface and metric .Code : route print .
45. Netstat
: This netstat command will shows you connection to your box.
46. Nslookup:
This nslookup command has many functionalities.One is for resolving
dns into ip. Lets say you know the website url but you don't know its
ip and want to find out. Now, another really nice function of nslook
up is to find out ip of specific mail servers.














































nyc post
ReplyDeleteits really nice one
ReplyDeleteThanks hope you are enjoying. For any doubts please comment
ReplyDeleteI'm curious to find out what blog platform you happen to be utilizing? I'm having some small security problems with my latest website and I would like to find something more safe. Do you have any recommendations? gmail sign in
ReplyDelete